-
Getting Started
-
Vulnerability Management
-
Reports
-
Other
-
FAQs
-
Features
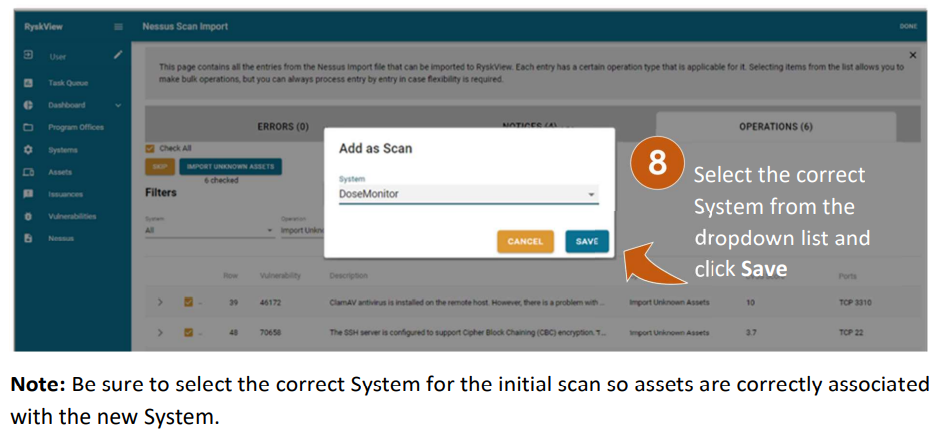
Ryskview accepts vulnerability scan imports from Tenable Security Center. The initial scan import is a critical step in the process as it will associate the imported assets with the correct system. For the initial scan import, the scan should be system specific. For example, a medical system scan should have its own scan, which is separate from the LAN scan. After the initial import, then multiple systems can be in the same scan import. You will follow these same steps to perform subsequent scan imports, which can be for individual or combined systems.
Note:
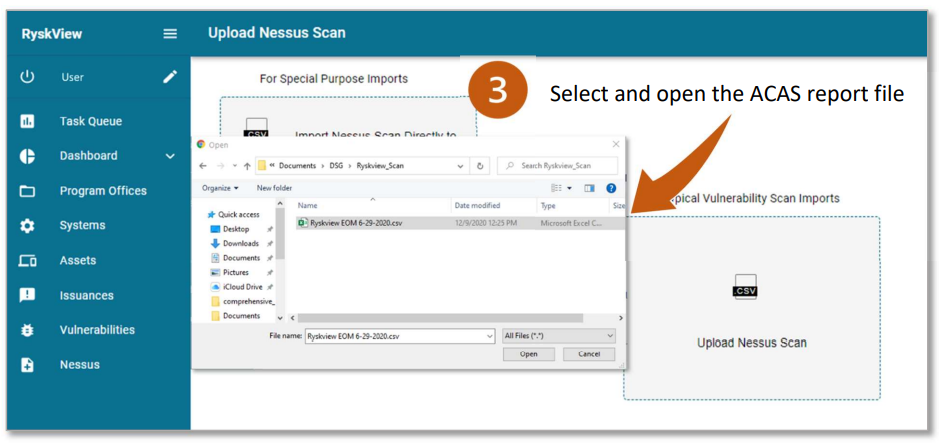
- Typically, an admin with access to Tenable.sc is responsible for exporting a report from Tenable Security Center using the Tenable Security Center CSV report format provided by Ryskview support.
- The CSV should NOT be opened and resaved in Excel, as Excel will corrupt the format of the CSV export. As a result, Ryskview will be unable to import the file.
- Tip: Copy the CSV export file so you can examine the copy without corrupting the original.
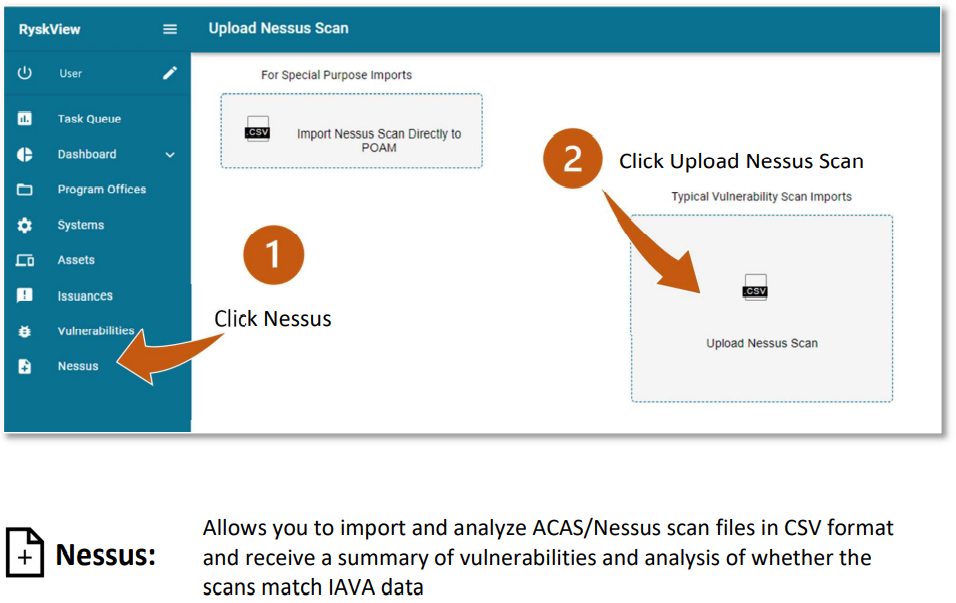
Vulnerability Scan can be uploaded to Ryskview manually. On the Nessus page, there are two options for imports: Typical Vulnerability Scans and Import Scans Directly to POAM. Specific headers must be used for Ryskview to accept the Scan file. Please reach out to Ryskview Support at dha.belvoir.fbch.list.ryskview-support@health.mil in order to receive a template .xml file needed to format the Scan export with the correct headers for Ryskview.
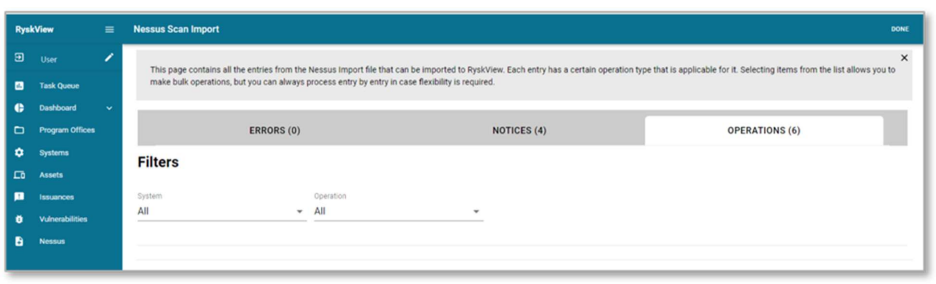
When Ryskview accepts the scan, a screen with 3 tabs will appear:
- Error – Identifies data and row in the import file that is unreadable by Ryskview
- Note: There is a header row in the file, so the problematic row is usually the row below. If you see an error that needs to be remedied, cancel the import, and reach out to Ryskview support personnel.
- Notices – Identifies informational checks used during the import. No action is needed here. It is purely informational.
- Note: There should be a notice identified by Plugin ID 19506 for each asset that was scanned. This notice includes whether the scan was credentialed or uncredentialled.
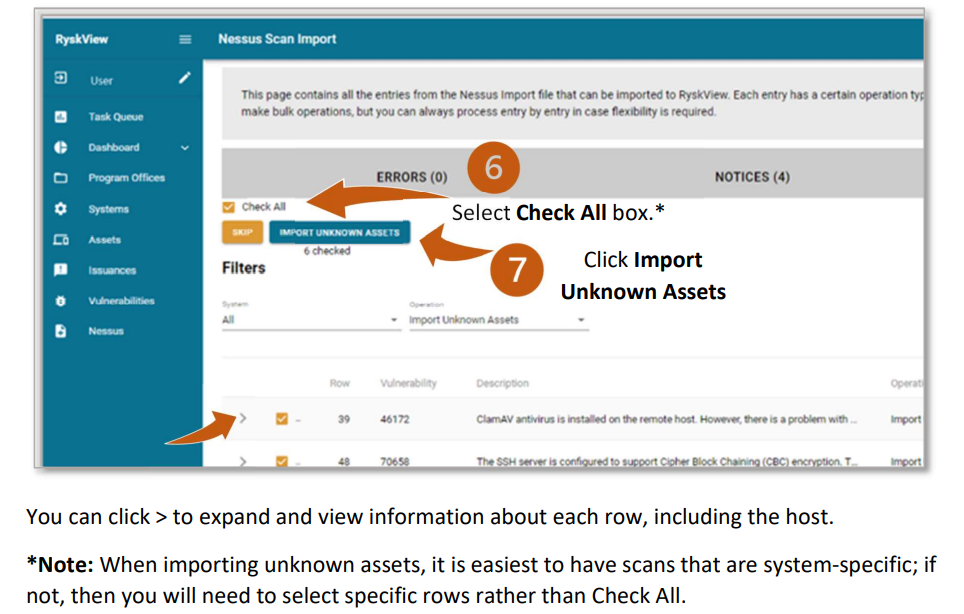
- Operations – Identifies Vulnerabilities for known and unknown assets inside Ryskview that can be uploaded
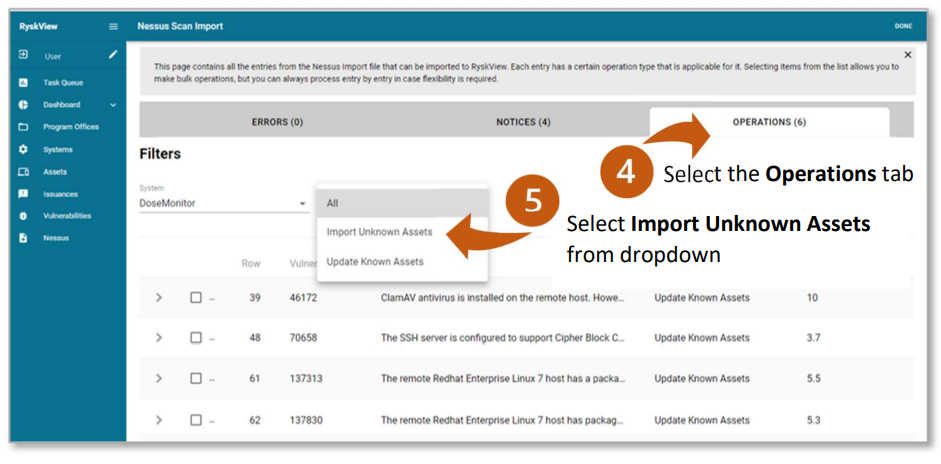
By default, the Operations filter is set to All. Other options include:
- Import Unknown Assets: Filters the import list to show assets that are unknown to Ryskview
- Update Known Assets: Filters the import list for all Assets that are known, or previously existing in Ryskview and already associated to a System