-
Getting Started
-
Vulnerability Management
-
Reports
-
Other
-
FAQs
-
Features
Introduction
The Controls Assessment Feature provides users the ability to track their compliance within DoD CCI or another type of framework. Users can access the controls assessment tab from the Systems page by selecting the action button of the preferred system, selecting view, and selecting the Controls Assessment tab.
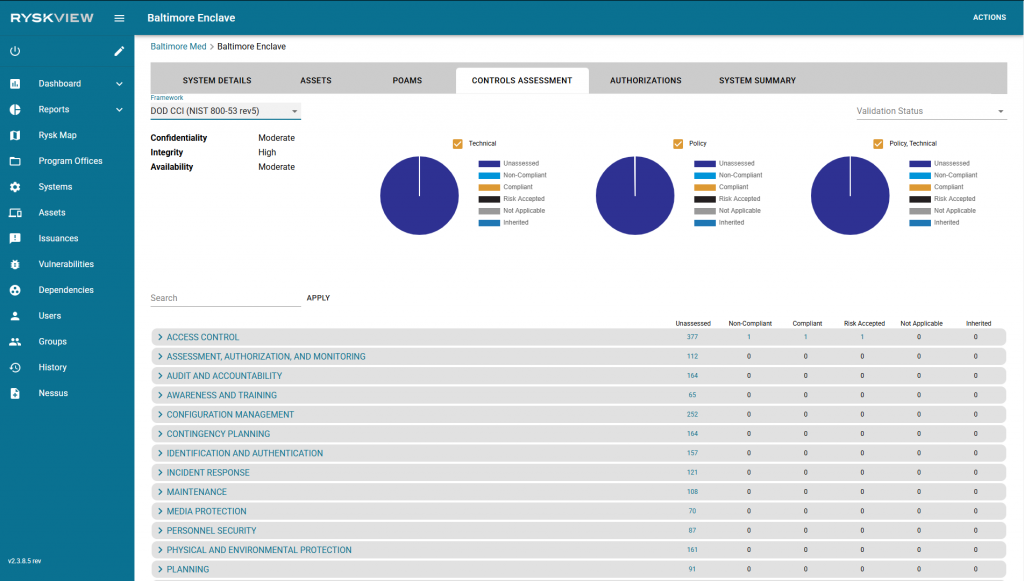
Select the framework dropdown menu in the top left corner to change the viewed framework. Displayed policies can be filtered by validation status using the dropdown in the top right corner. The validation statuses are Unvalidated, Ready For Validation, and Validated.
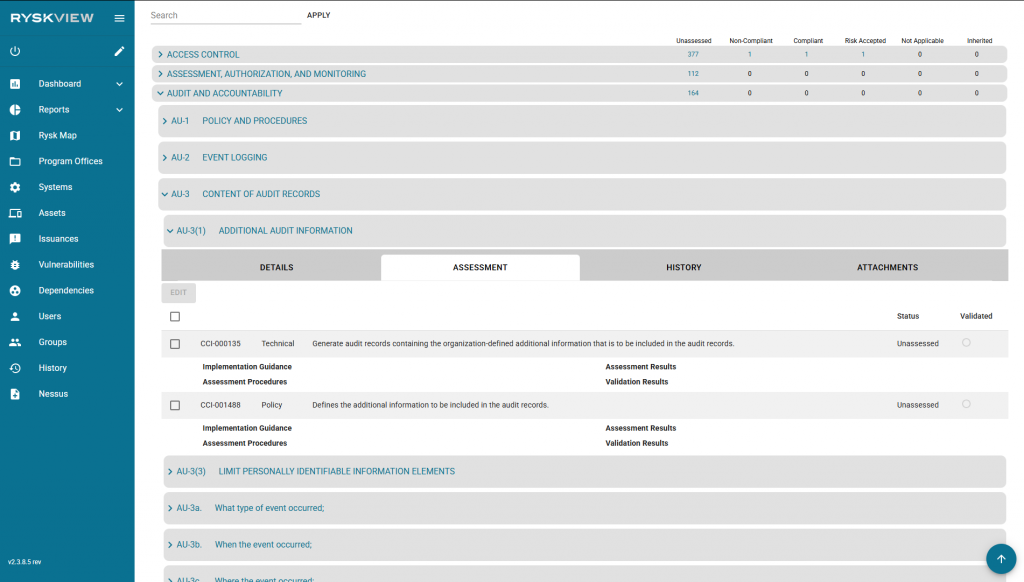
Users can navigate through the policies using the dropdown arrows next to the policy category. Each policy has four tabs showing the details of the selected policy, the assessments of the policy, the history of actions taken on the policy, and any attachment uploaded in reference of the policy. Under the assessment tab, user can change the assessment by selecting the checkbox on the left side and selecting the edit button in the top left corner of the assessment tab. The checkbox directly below the Edit button will select all assessments in the tab. User can change the status and validation of the assessment using the dropdown menu in edit mode. Clicking the save button will save the changes made for the selected assessments.
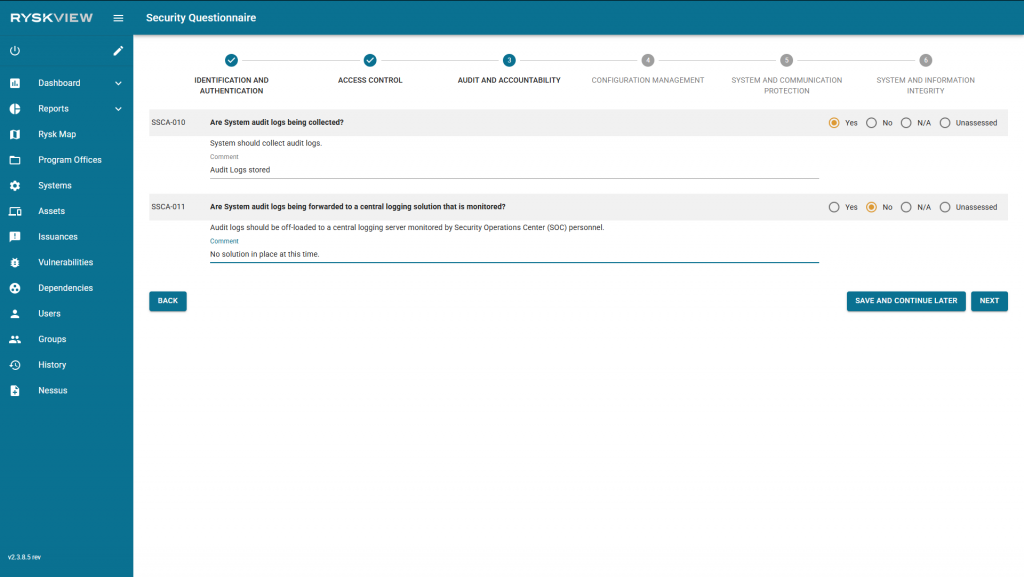
Simple Security Questionnaire
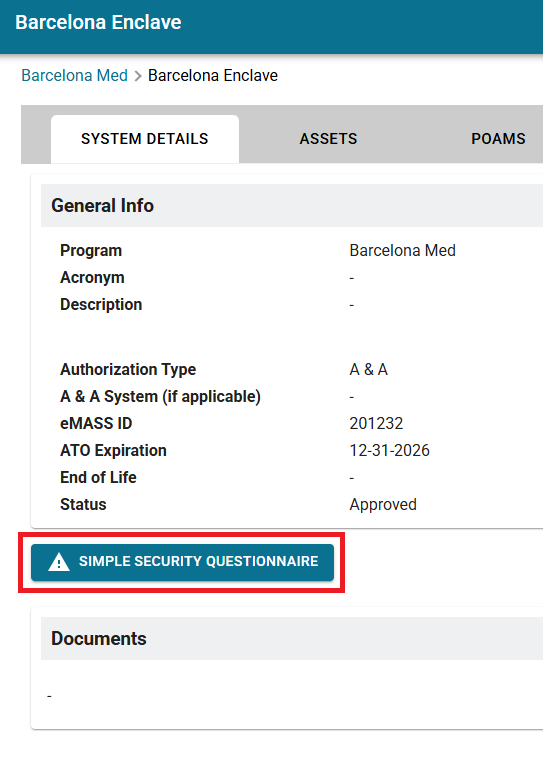
Ryskview has designed a 30 question questionnaire to simplify the process of assessing how proficient a system is to the Simple Security Controls Assessment Framework. Filling out the questionnaire would auto-populate the framework based on the answered questions. Users can access the questionnaire by selecting the Simple Security Questionnaire button, highlighted in the image below.
The questionnaire has five topics with varying numbers of associated questions. The topics include:
- Identification and Authentication
- Access Control
- Audit and Accountability
- Configuration Manangement
- System and Communication Protection
- System and Information Integrity