-
Getting Started
-
Vulnerability Management
-
Reports
-
Other
-
FAQs
-
Features
Ryskview organizes the hierarchy of information into three groups: Program Offices, Systems, and Assets. This structure allows users to properly outline the boundaries of their information systems and the responsibilities of each device that falls within them.
Program Offices
Program Offices are the highest tier in the hierarchy. They are typically a physical location where a group of information systems resides. In Ryskview Program Offices are composed of one or more systems. Users and groups can be given program administrator permissions to a specific program office. These permissions will permit the user/group access to roles to systems under the Program Office.
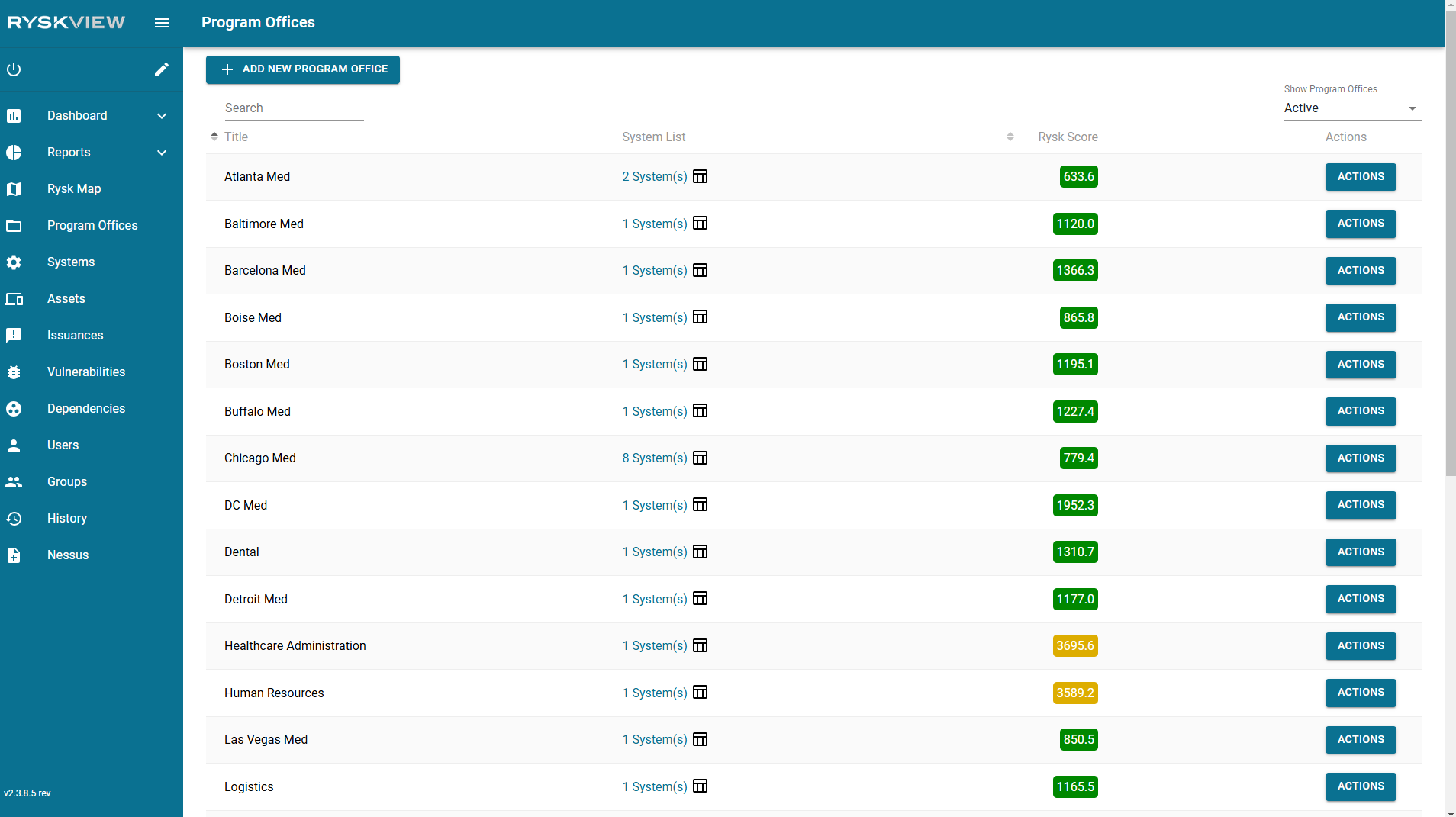
Above is an image of the Program Office Page. Here is a breakdown of the columns on this page and their description:
-
- Title – Name of the Program Office. The names are unique.
-
- System List – Numerical value of systems in the Program Office. The icon next to the value, when clicked, shows the Authorization Matrix for the Program Office.
-
- Rysk Score – A cumulative score based on the average of the systems within.
-
- Actions – Action button. You can View more details of the Program Office, Edit the Permissions of the Program Office, or View the Authorization Matrix from this button.
Systems
Systems are next in the list of hierarchy. Systems are the information system groups within the Program Offices, which are composed of one or more assets. A key feature of the system structure is the ability to categorize assets from imported data into their respective boundary.
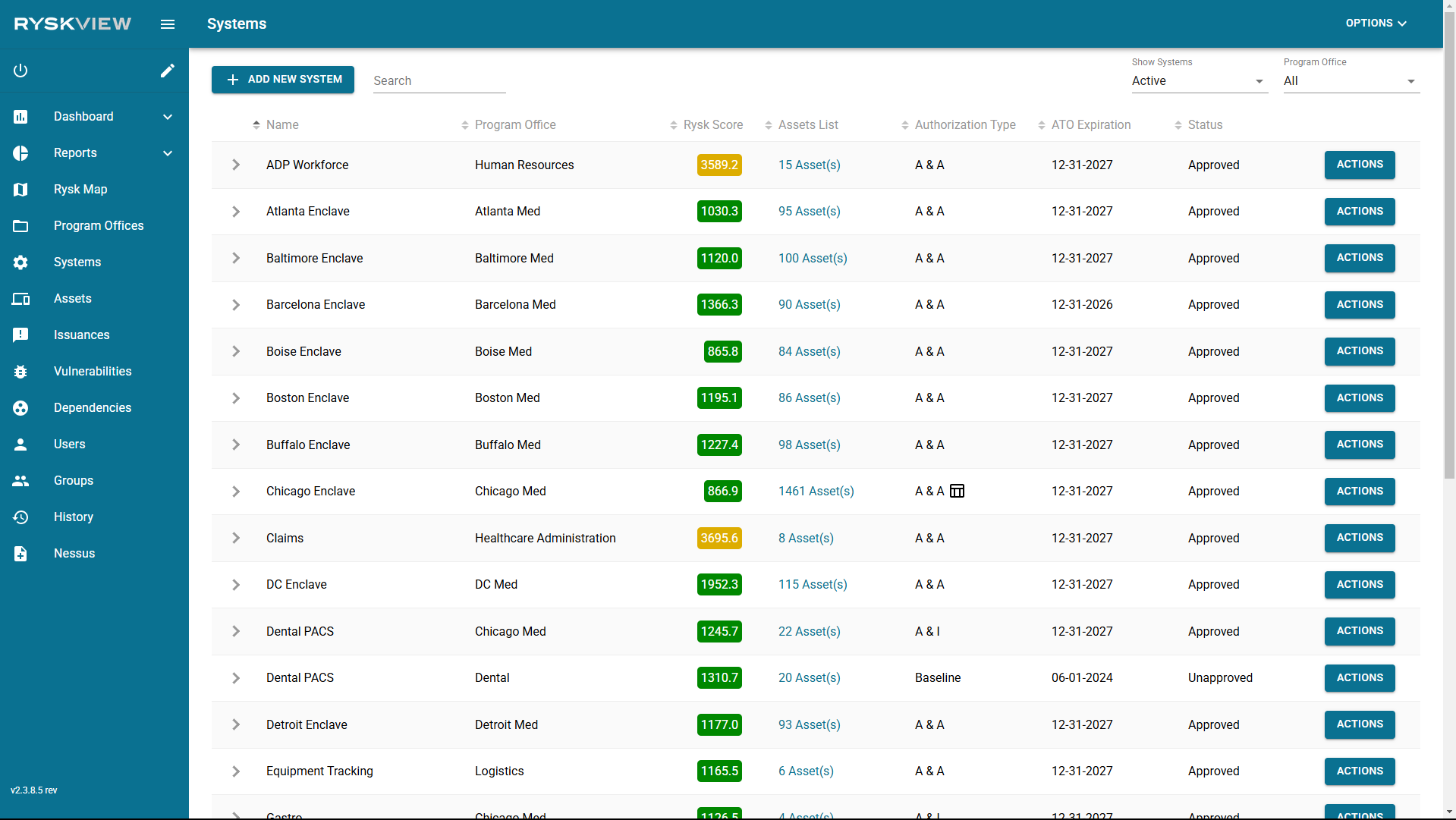
Above is an image of the Systems Page. Here is a breakdown of the columns on this page and their description:
-
- Name – Name of the System. The names are unique to the Program Office.
-
- Program Office – Name of the associated Program Office.
-
- Rysk Score – A cumulative score based on the average of the assets within.
-
- Assets List – Numerical value of assets in the system.
-
- Authorization Type – The ATO authorization type for the system. Options are Assess and Authorize (A & A), Assess and Incorporate (A & I), Baseline, and Deployment. The icon next to the value, when clicked, shows the Authorization Matrix for the System.
-
- Actions – Action button. You can View more details of the System, and Edit the permissions of the System.
Assets
Asset are the information system devices that make up the Systems in Ryskview. Asset can be laptops, servers, switches, medical devices, as well as a number of different devices that make up a information system.
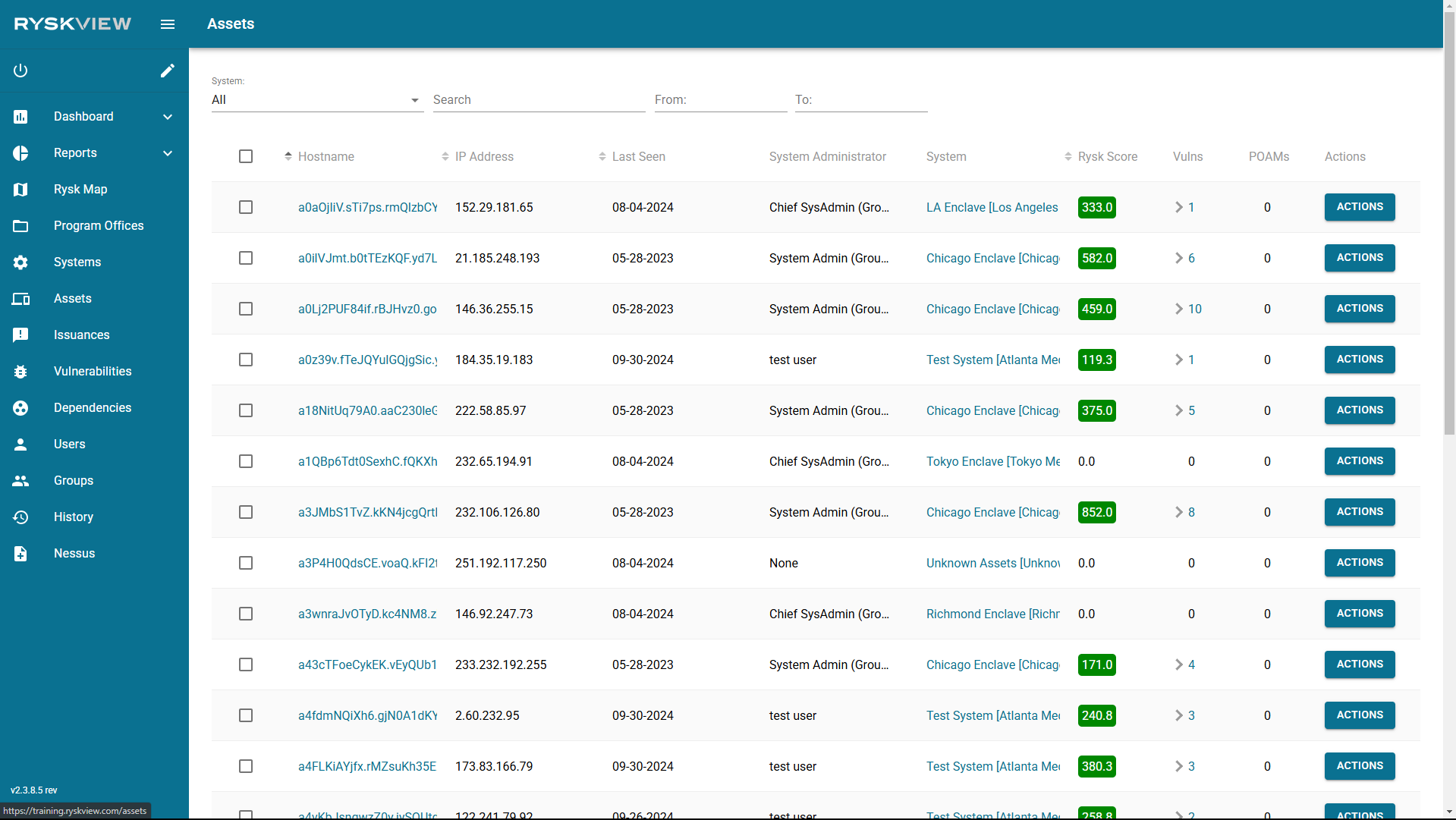
Above is an image of the Assets Page. Here is a breakdown of the columns on this page and their description:
-
- Hostname – Name of the Asset. Each asset name is unique in Ryskview.
-
- IP Address – The IP address of the asset
-
- Lase Scene – The latest date the asset was seen on a scan.
- System Administrator – The associated user or group responsible for the system.
-
- System – The associated system the asset belongs to.
-
- Rysk Score – A cumulative score based on the average of the assets within.
-
- Vulns – Numerical value of vulnerabilities on the asset.
-
- POAMS – Numerical Value of vulnerabilities on a POAM for the asset.
-
- Actions – Action button. You can Edit the details of the Asset, Move the Asset to another System, and Delete the asset from Ryskview.
