-
Getting Started
-
Vulnerability Management
-
Reports
-
Other
-
FAQs
-
Features
Ryskview allows for the export of Report data in to a CSV, which can then be used to create informative and flexible PivotTable Reports and Graphs in Excel. Below are directions on how to create a simple PivotTable Report to see Vulnerabilities across multiple Program Offices and/or Systems or just within one System. Or to create a PivotTable Report of the Assets with the most Vulnerabilities.
- Go to Reports > Scan Data – Risk by System. Filter for appropriate Program Office/System.
- Filter Status = Past Due. (Optional. This can also be filtered within the PivotTable after Export).
- Export CSV.
- Open CSV and save as xlsx.
- Select all by clicking the top left corner of spreadsheet or Ctrl+A.
- Select Insert > PivotTable from menu bar. Populate table as desired.
To List by Vulnerability
Drag System Name and Title into the Rows field and Host into the Values field as shown below. You can also add Severity to Column or other fields to provide more information.
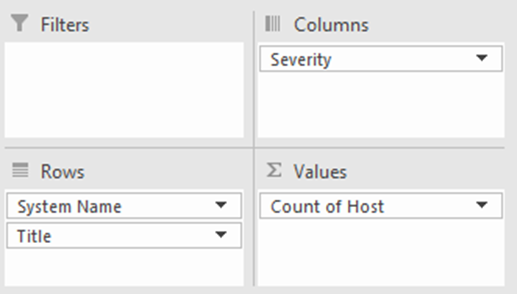
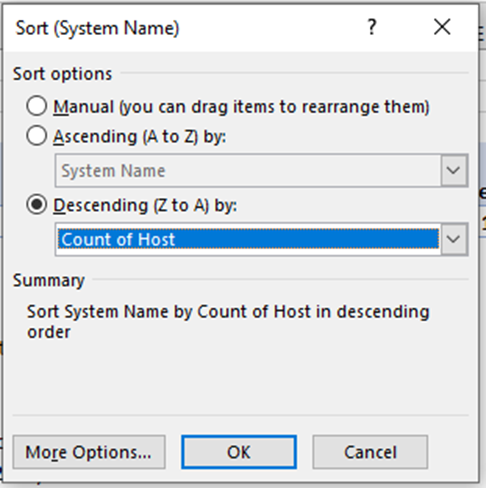
These can be sorted by number of each vulnerability (most to least) by clicking the icon for Row Label and then selecting More Sort Options, then Descending (Z to A) by: Count of Host as shown in picture below.

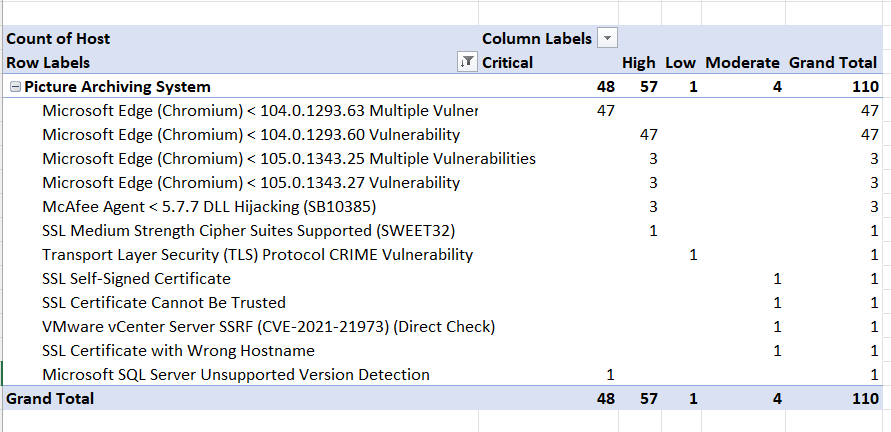
The Vulnerability PivotTable will look similar to the below.
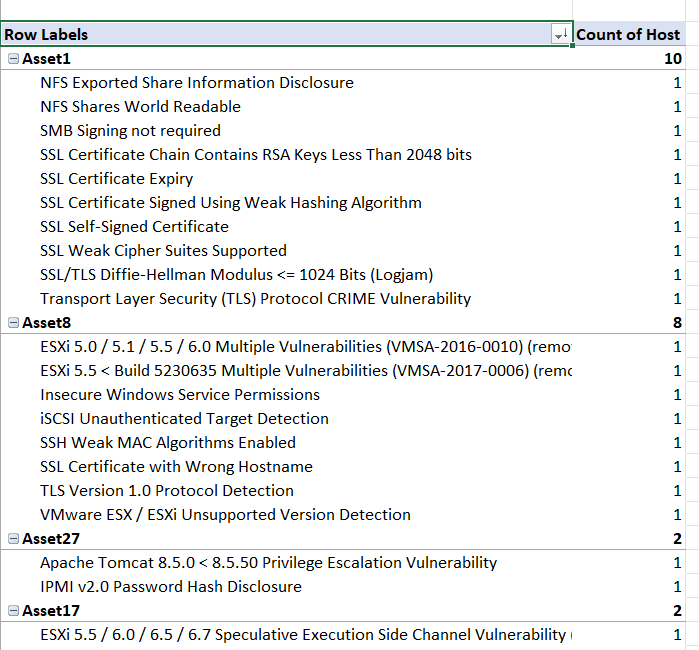
To List by Asset
Drag Host and Title into the Rows field and Host into the Values field as shown below.
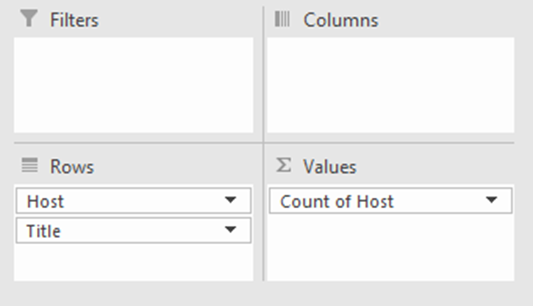
These can be sorted by number of each vulnerability (most to least) by clicking the icon for Row Label and then selecting More Sort Options, then Descending (Z to A) by: Count of Host.
The Asset PivotTable will look similar to the below.
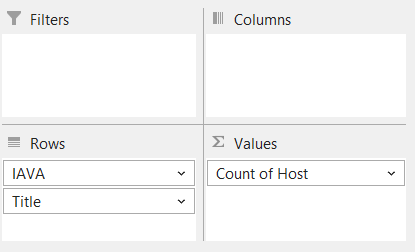
IAVAs
Drag IAVA and Title into the Rows field and Host into the Values field as shown below.
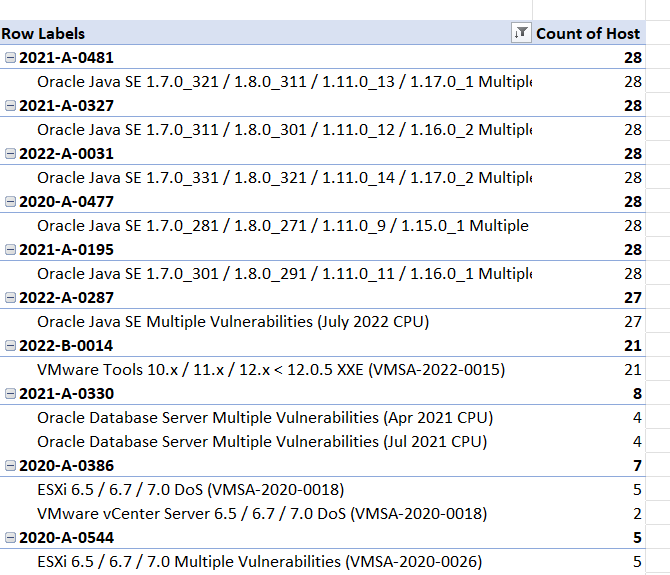
These can be sorted by number of each vulnerability (most to least) by clicking the icon for Row Label and then selecting More Sort Options, then Descending (Z to A) by: Count of Host.
The IAVA PivotTable will look similar to the below.
Last Seen Date
If you want to only see vulnerability data that was last seen within a specified time period, you can also filter the data based upon the Last Seen field. Add Last Seen to the Filter field and then select and edit as desired.
Conclusion
There are infinite ways of manipulating a PivotTable. If you have any questions or need assistance, please reach out to Ryskview Administrator.
