-
Getting Started
-
Vulnerability Management
-
Reports
-
Other
-
FAQs
-
Features
Importing Assessment Results
Ryskview can import results of ANY assessment. By utilizing the Ryskview Assessment Import Template (link below), you can cut and paste the results of any manual or automated assessment into the template for easy import.
Once the template is populated, log into Ryskview. On the menu bar, select “Nessus”, then select the smaller box in the top left labeled “Import Nessus Scan directly to POAM”. Select your file.
(If you get an error, see below for troubleshooting).
The screen will bring you to the Nessus Scan Import page.
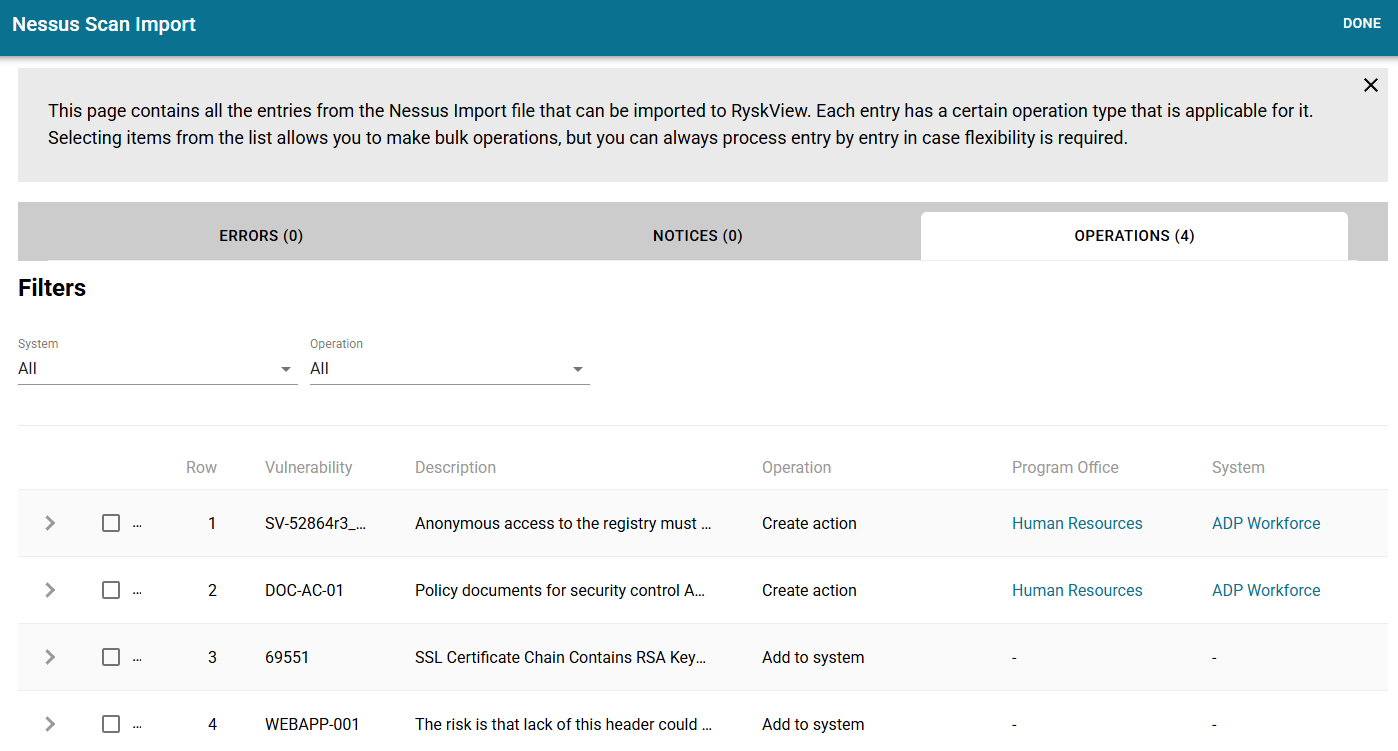
If Ryskview knows the Asset, then it will display in the operation column to “Create Action” and list the System and Program Office. If the Asset is unknown to Ryskview, then it will display “Add to System”.
In the “Operation” dropdown, select “Add to System”. The check then “Check All” box. Then click the “Add to System” button.
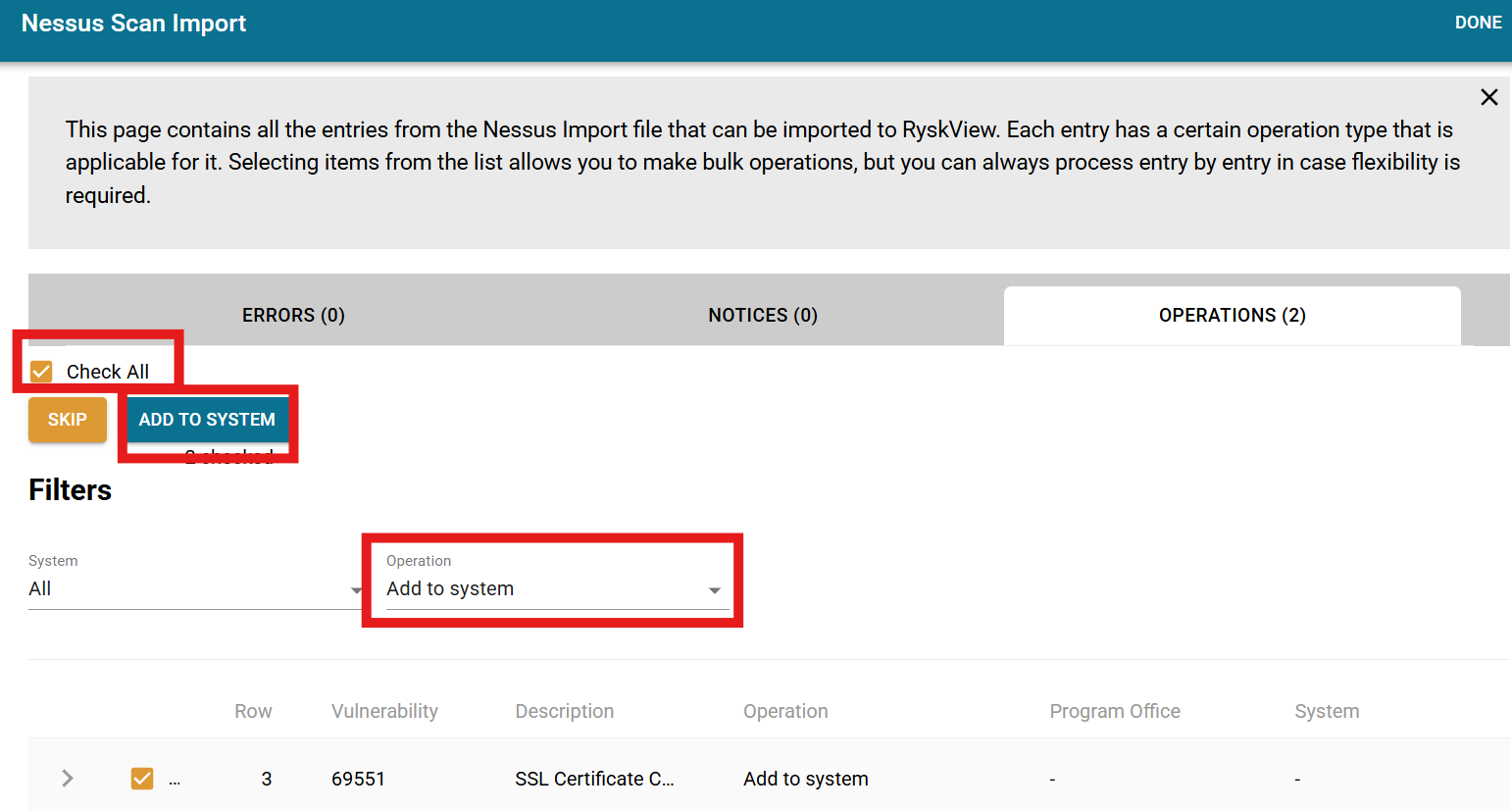
A modal will appear for selecting a System. Once the System is selected, the modal will allow you to add the open finding to an existing POAM or create a new one. Typically, you will create a new POAM, give it a name (usually descriptive of the assessment type/tool), and then select the workflow. The default workflow is “System Admin –> ISSO”, which would assign the finding to the System Admin, but you can choose a different workflow if appropriate.
This will create the Asset, link it to the System selected, and create an Action item on a POAM.
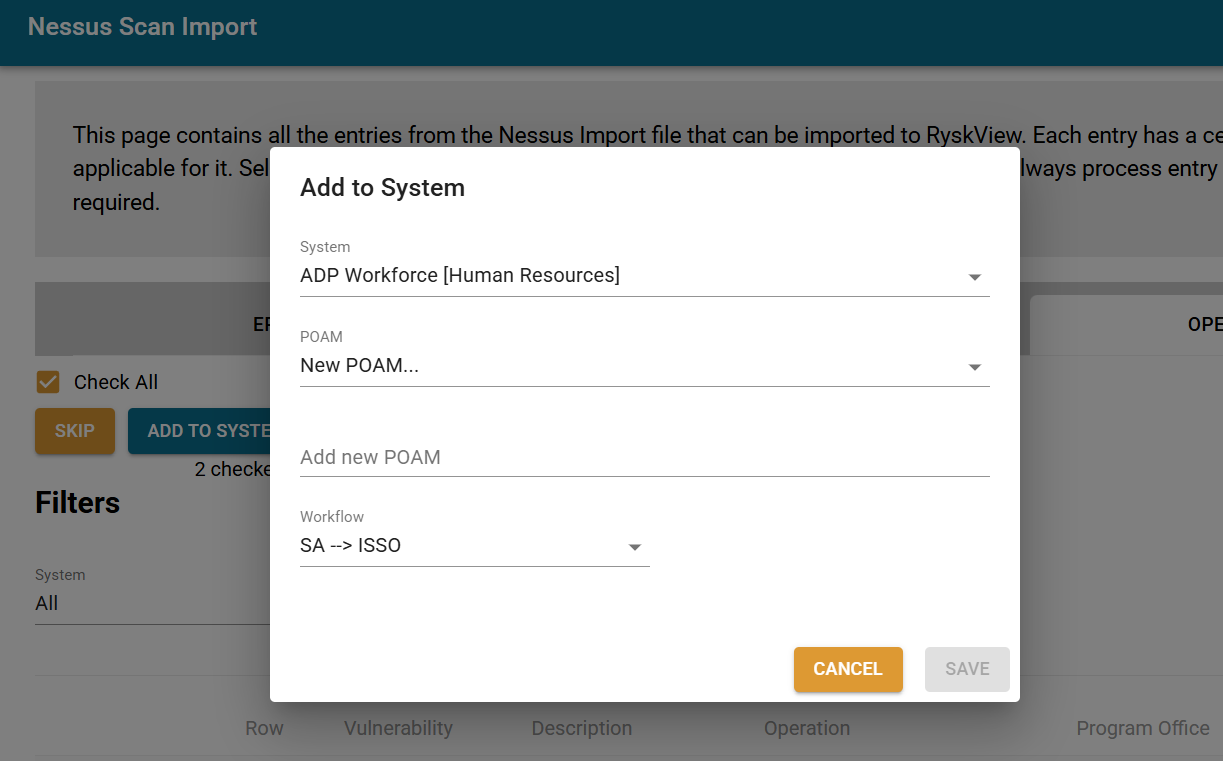
Once you have added all the unknown Assets to a POAM, it is time to add the known Assets. In the “Operations” dropdown, select “Create Action”. Select the “Check All” box, and then click “Create Action” button. Select the appropriate POAM (or create a one). If creating a new POAM, give it a name (usually descriptive of the assessment type/tool), and then select the workflow. The default workflow is “System Admin –> ISSO”, which would assign the finding to the System Admin, but you can choose a different workflow if appropriate.
This process of “Create Action” will add the assessment findings to the POAM that you selected.
Using the Import Template
Download the template linked at the top of this article. Please note that the file is a CSV format with specific column headers. Do not change the column headers.
There are four assessment findings populated as examples. Be sure to delete these rows before importing the file into Ryskview. Below is a description of each column field. Required fields are notated by and asterisk.
Plugin*
This is a unique identifier of the vulnerability, or finding. This can a standard UID such as a STIG ID or can be created by the user.
Plugin Name*
This is a name or title of the vulnerability.
Severity*
Severity can be Low, Medium, High, or Critical.
DNS Name*
This identifies the Asset that has the vulnerability. IT can be the DNS or hostname or any reference to the Asset.
IP Address
The IP address is not a required field, but it should be populated, when the IP is known. Do not include the subnet.
Protocol*
This is typically TCP, though can also be UDP, ICMP, or other appropriate protocols.
Port*
If the vulnerability has no port, or it is not applicable, just enter a zero.
MAC Address
This is optional, but helpful in documenting specific Assets.
Description*
This is an explanation of the vulnerability.
Plugin Output
This field is for entering any information specific to the assessment of the Asset. For example, it may be the file version of the non-patched software, the reason for the failed assessment, or evidence of the failed assessment result.
Solution
This is where fix information or guidance for remediation would be placed.
First Discovered*
This is the date and time the vulnerability was first found. It must be formatted correctly as seen below.
“Jan 21, 2025 12:46:12 EDT”
Last Observed
This is the most recent date the vulnerability was assessed. This will usually be the same as the First Discovered date. Last Observed cannot be earlier than First Discovered. It must be formatted correctly as seen below.
“Jan 21, 2025 12:46:12 EDT”
Once the Assessment results in the file are populated, save the file (as CSV) and then follow the procedures detailed above to import directly to a POAM.
The Dashboard is the landing page after logging into Ryskview. It is customized to each user based upon their designated roles such as System Admin, ISSO, CIO, etc). Each tab is role-based, so a user may have more than one tab, if designated as more than one.
The Dashboard consists of multiple informational tiles. Tiles can be which can be hidden by unpinning them. To restore a tile, scroll to the bottom of the Dashboard and click on the Tile you would like to restore.
To Do List
The To Do List is a designed to provide the user with specific tasks that need to be taken. The goal is to reduce each of these metrics until they reach zero
Past Due Vulnerabilities without a POAM – The number shown indicates the number of Systems that have vulnerabilities that have exceeded their due date. Clicking on the value opens a dialog box displaying the System Name, the Program Office, and Rysk Score. Clicking on the System Name will display the Assets in that System that have overdue vulnerabilities.
In order to address this metric, click on “Scan Data” button at the top of the Dashboard page, or navigate via the menu bar Dashboard > Scan Data.
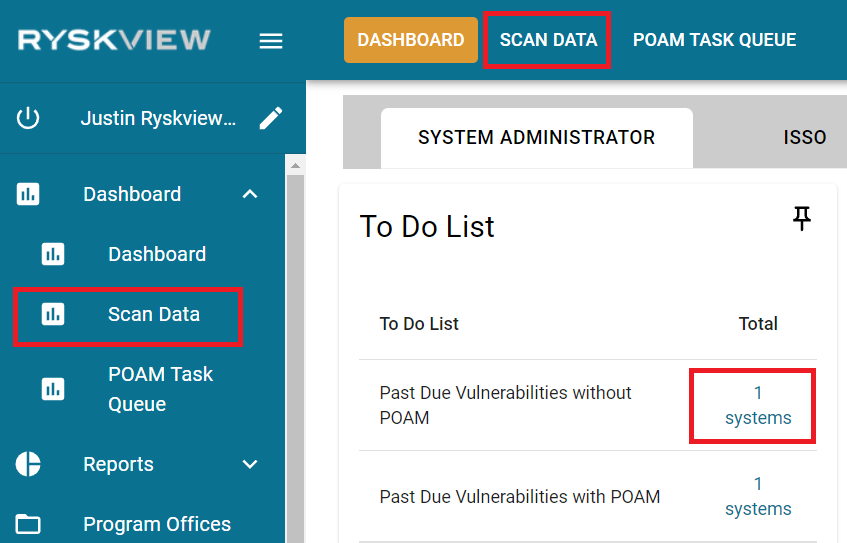
Once Scan Data page opens, look at the column “Past Due w/o POAM” and address by either remediating or Adding to POAM.
Past Due Vulnerabilities with POAM – The number shown indicates the number of systems that have POAMs that are past their Scheduled Completion Date (SCD). Clicking on the value will open a new tab in the browser, load the user’s POAM Task Queue, and filter the POAMs for just those that are Past Due.
In order to remediate, add a new milestone that extends the SCD.
POAM SCD less than 30 days – The number shown indicates the number of POAM items that have a Scheduled Completion Date (SCD) within the next 30 days. Clicking on the value will open a new tab in the browser, load the user’s POAM Task Queue, and filter the POAMs for just those that are due within the next 30 days.
.In order to remediate, address the POAM item and/or add a new milestone that extends the SCD.
POAMs ready for closure (not on recent scan) – The number shown indicates the POAM items that have zero vulnerable assets. In other words, recent scan has validated that the vulnerability no longer exists on the Asset, and therefore the POAM can be closed.
Uncredentialed Scans – This number indicates the Assets that the most recent scan was uncredentialed. Clicking on the value will display the specific Assets that are identified. Scans are more accurate when credentialed, so when possible, they should be credentialed. By default, Ryskview requires all Assets to have credentialed scans, but this can be changed for specific Assets.
In order to reduce this number to zero, contact the Scanning Administrator and ensure that they have proper credentials to scan the Assets listed.
Alternatively, if there are Assets that are not expected to have credentialed scans such as certain medical devices, ICS/OT system components, or IoT, then the user can Edit the Asset properties and uncheck the “Require Credentialed Scans” attribute.
Unknown Asset Type – This number indicates the Assets that have not been categorized as a Type. Clicking on the value will open the Asset page and display only the Assets that are both uncategorized and fall within the responsibility of your role.
Categorizing the Asset Type is important both for asset management purposes, but also for Rysk Scoring. Asset Type is one of many components that help determine the Rysk Score.
System Authorization – This number indicates the pending tasks awaiting authorization from the user. Clicking on the number will pop up a modal, displaying the systems with pending tasks. Clicking on the system will display a new window of the System’s Authorization tab.
Systems
The Systems tile provides information regarding System Authorizations and Compliance, as well as identifying the High Risk Systems. While there is nothing explicitly actionable, the goal is to provide a summary of information as well as highlight the High Risk Systems, so that the user will investigate and reduce the risk of these Systems. The High Risk value is hyperlinked so the user can click and see exactly which Systems are being identified.
A & A / Baseline / Deployment – This indicates the RMF Effort Type selected for these Systems.
Approved – These are the Systems that have a valid ATO Expiration date in the future.
ATO expires in less than 60 days – These are the Systems where the ATO expires within the next 60 days.
ATO Expired – These are the Systems where the ATO Expiration date has already passed.
Assets
The Asset tile identifies that different Asset Types, as well as identifying the High Risk Assets.
The Asset Types are are classified by the users of the application by going to the Assets page, editing one or more Assets, and selecting the correct Asset Type from the dropdown menu.
Operating Systems (OS)
The OS Tile lists the Operating Systems that are present, as well as identifying the High Risk Assets with specific Operating Systems.
