-
Getting Started
-
Vulnerability Management
-
Reports
-
Other
-
FAQs
-
Features
(However, in order to view the Baseline data, the Deployment users would need to update permissions. Likewise, in order for the Baseline System users to see the Deployment System data, they would need to update their permissions as well.)
Other than just documenting the Authorization relationship for Baseline/Deployment Systems, Ryskview also gives the capability to compare the security postures of the varying systems from both the Baseline, or Program Management perspective, as well as the Deployed Site perspective.

Baseline Profile Columns
Deployed Systems
Clicking on the VIEW DETAILS button will provide specifics for the Deployed System as shown below.

Document Details provides the specific compliance for each of the three required documents.
Scan Data provides the same metrics for the Deployed System that are provided for the Baseline System.
POAM Details indicates the number of POAM items that are past due.
Clicking COMPARE TO BASELINE will provide a vulnerability specific comparison to the Baseline System as shown below.
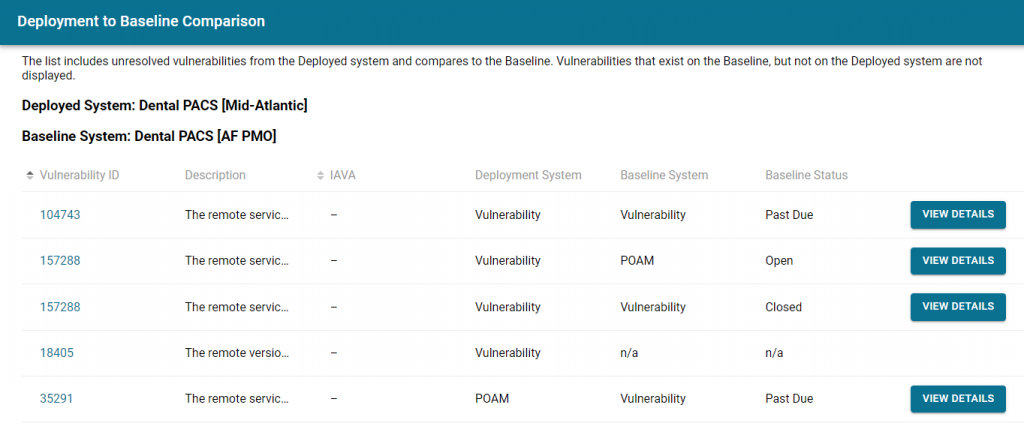
Deployment to Baseline Comparison
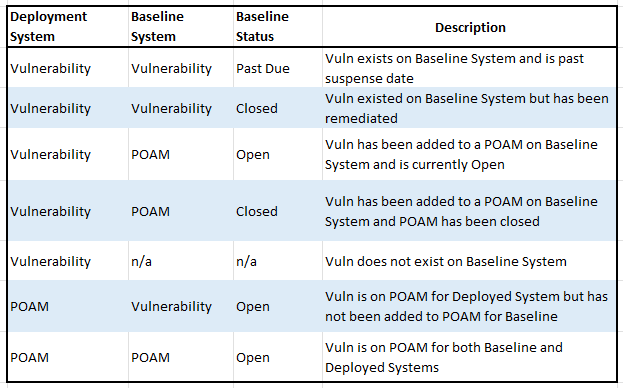
This view is from the perspective of the Deployed System. It lists all the open vulnerabilities, Scan Data and POAMs, for the Deployed System and provides the status of that same vulnerability for the Baseline System. If a vulnerability exists on the Baseline System, but not on the Deployed System, then it will not show up in this view. Below is a chart to help understand the meanings.
Selecting VIEW DETAILS will provide the specific details of the vulnerability on the Baseline System.
FAQ: How can a vulnerability show up on a Deployment but not on a Baseline System?
A: There are more than a few ways this can happen. The specific reason will always become apparent by looking at the vulnerability itself. Below are a few examples.
1. An SSL Certificate related vulnerability. It is possible to have different SSL certificate configurations on Baseline and Deployment.
2. Virtual Server related vulnerability. If the Deployment is virtualized, an ESXi or VMware related vulnerability may occur.
3. Configuration related vulnerability. If the Deployment has certain configurations that are not aligned with the Baseline, such as Autologon Enabled, a vulnerability may occur.
4. Software related. If the Deployment has software installed that is not installed on the Baseline, then a vulnerability for the software may occur.
